API Gateway Security

An API gateway is an essential component of an API management solution. It is key to API security and protects the underlying data like a gatekeeper checking authentication and authorization and managing traffic. In this post we’ll discuss how an API gateway works, and the 10 most significant threats to API security today. You’ll also discover why it is absolutely mandatory to have an API gateway when offering and consuming APIs.
API Gateway Security – What is an API Gateway?
The API Gateway is an important part of an API solution. API Gateways enforce policies which control security aspects such as the authentication, authorization or traffic management. The API Gateway is comparable to a gatekeeper guarding the underlying data. API Gateways such as SEEBURGER’s provide transparency in API-related traffic and enable the fulfillment of API demands set by the market and line of business.
API Gateway Security – Implemented by Policies
Policies are rules that serve to design and secure the underlying services and therefore determine the behavior of the API. Policies can be assigned to different groups, such as traffic management or authentication/authorization. The structure of a policy is always the same – at least one rule to be checked and the resulting action to be executed. All of this happens inside the API gateway, which is responsible for policy enforcement. The policies can be implemented at different levels:
- Method level: The policy applies to that specific method, e.g. getOrder.
- Resource level: The policy applies to a specific resource and the underlying methods.
- API level: The policy applies to the complete API.
API Gateway Security – Policy to Manage the Traffic
It is important to restrict the number of times an API can be called within a certain time range, for example, to protect the backend systems which can only handle a certain amount of requests in a certain time period, or to protect against DoS attacks. This is done with the help of a “Rate Limit By Key” policy. The policy consists of 5 parts.
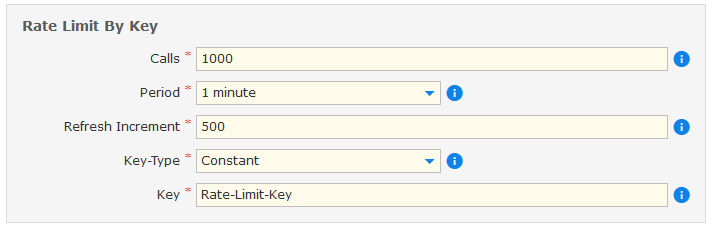
- Calls: Possible amount of calls within the time frame.
- Period: Represents the time frame. After the chosen time frame is expired, the calls are refreshed and available again.
- Refresh Increment: Amount of calls, which will be refreshed after the chosen period. If calls is equal to refresh increment, all calls will be refreshed. But it is also possible, just to refresh a certain amount of calls, e.g. 500 of 1000.
- Key-Type: Specifies the type of key necessary for the limitation.
- Key: Specifies the key for which the call counter is increased.
API Gateway Security – Policy to Check a JWT
A JSON Web Token (JWT) is an access token that contains rights for the calling user. JWTs are often used if an external Identity Provider is in place. The policy checks whether the incoming API call contains a JWT and whether it is valid. In the second step, the contained rights are checked with those specified in the policy. If the required / specified rights and the rights in the JWT do not match, the API call is blocked. Read our article on API Authentication to learn more about JWT.
API Gateway Security – what the API Gateway protects against
There is a large number of possible threats and attacks in the API environment . The Open Web Application Security Project, OWASP, published the most recent threats, which include:
- Broken Object Level Authorization
- Broken User Authentication
- Excessive Data Exposure
- Lack of Resources & Rate Limiting
- Broken Function Level Authorization
- Mass Assignment
- Security Misconfiguration
- Injection
- Improper Assets Management
- Insufficient Logging & Monitoring
All OWASP API Security Project documents are available for free.
It is important to note that the API Gateway and its policies play an important role in API security, but it doesn’t cover anywhere near all the possible threats. A more comprehensive picture including general API design and more is necessary.
Do you want to know more about APIs? Read our blogs What is API integation, What is API management and our survival guide APIs – from API Management to API Solution.
Thank you for your message
We appreciate your interest in SEEBURGER
Get in contact with us:
Please enter details about your project in the message section so we can direct your inquiry to the right consultant.
Written by: Tim Allgaier
Tim Allgaier was working as Technical Product Manager at SEEBURGER since 2019 for Business Integration Suite. His focus was on the topic of API Management. During his master's degree in Business Informatics, Tim Allgaier worked in different positions in the subject area of software management and IT service management. In his time off, Tim Allgaier is mainly engaged in sports activities like table tennis.