Understanding phishing attacks and protecting valuable data Part II

Fake invoices, phishing e-mails and the distribution of malware via download links are a constant threat to companies and private individuals alike. After we dealt with the question ‘What are phishing emails?’ in the first part of this blog, we will now explain how fraudulent phishing emails work and how you can protect your company, based on a real-life customer story.
The initial Situation
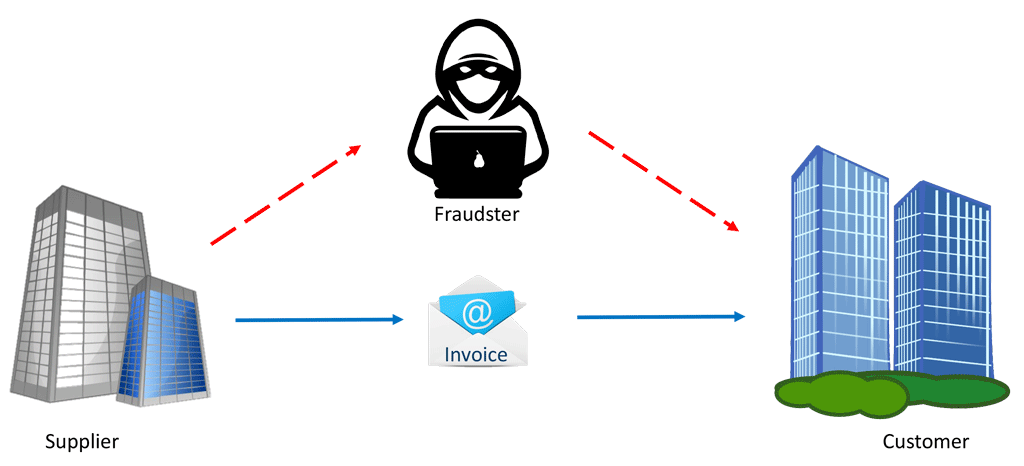
A German supplier received an order worth more than 100,000 euros from a customer in a non-European country. The services were rendered, the supplier sent an e-mail invoice, and the customer paid it promptly to benefit from the discount granted and was satisfied until – yes, until he received a message from the German supplier reminding him of his outstanding invoice amount. The customer checked his account balance with the certainty that he had paid the invoice long ago. And correctly, the amount had been deducted from his account. But it had never been credited to the account of the German supplier. What had happened? The customer had fallen victim to a phishing attack.
How Phishing Attacks Work
In fact, financial transactions between companies involving sums of over 100,000 euros are very popular targets of so-called phishing attacks. This is because the ‘swindling’ of such large amounts justifies the considerable effort that a fraudster has to make to stand a chance of acquiring the money:
- The first step is to illegally obtain a copy of the e-mail from which the supplier’s invoice was sent. To accomplish this, a Trojan first needs to be installed at the sender or recipient of the e-mail in order to intercept the e-mail, as described in the first part of this blog. Once the fraudster is in possession of a copy of the invoice, they have all of the data for the invoice recipient at their disposal and can use this for their own purposes.
- Next, the fraudster, who in our case is based in an African country, registers an Internet domain that is confusingly similar to that of the supplier. If the supplier’s original domain is ‘supplier.com’, for example, they only falsify it very slightly, so that the customer has to look very carefully to see that this is a ‘mistyped domain’. Popular are for example duplications like ‘nn’ instead of ‘n’ or letters that look very similar to ‘I’ and ‘l’ or ‘m’ and ‘n’, ‘v’ and ‘w’ or even ‘O’ and the number ‘0’. Even letter turners are read over by our brain. So the ‘typo domain’ ‘suppIicom’ with a capital i instead of low key ‘L’ would hardly attract attention.
- Alternatively, the fraudster can create a fake country domain with the supplier’s company name. After all, the customer won’t know whether the supplier has registered another internet address in other domains, for example ‘.eu’ or ‘.biz’ or other top level domains. For such misuse, large ‘hosters’ with automatic and fast ordering processes are commonly used, where a stolen credit card or invalid bank details are not immediately noticed. A domain is usually set up within a few minutes and can then be used for a few days before the fraud is discovered.
- Now the fraudster creates a similar invoice based on the stolen invoice data, only with the difference that the bank details of the supplier are exchanged for the fraudster’s bank details. Especially in international business transactions with companies in different countries, it quite common for a German company to maintain a bank account in another country, for example in close proximity to the customer – especially if the supplier has a branch office on site. This saves on the fees incurred for foreign bank transfers. In order to illustrate these relationships clearly, we also chose a customer abroad for our example. Large companies often even operate an internal cash management system with clearing in order to optimise the movement of money.
- If the original e-mail from the supplier was signed, it requires only a small amount of additional work for the fraudster as the ‘owner’ of the ‘mistyped domain’ to obtain a signature for sample@suppIier.com as well. Even the corresponding security filters with SenderID, DomainKey etc. cannot work, because the fraudster sends an e-mail from a valid domain that belongs to them.
- The fraudster then sends the fake invoice e-mail to the customer as ‘sample@suppIier.com’ and can even ‘speed up’ the transfer with particularly high discounts, so that the customer may not look too closely.
- Finally the e-mail of the fraudster from Africa reaches the in-box of the customer instead of the original message of the German supplier and the customer unsuspectingly settles the manipulated invoice with the wrong account details.
The supplier in Germany is not aware of any of this. Nor do they know that the invoice may have been intercepted by a Trojan on their own system.
Secure Invoice Delivery
As already described in our first blog on this topic, a digital signature is hardly sufficient for e-mail invoices.
Invoices can only be sent securely via an encrypted transmission with a separate password (e.g. via SMS dispatch), as used with SEEBURGER’s Managed File Transfer (MFT) solution. The SEEBURGER Invoice Delivery Service offers such security. The invoice recipient receives a link to the secure download. With this link they register with a user name and password. Theu receive this via a separate communication channel. They can then download the invoice in encrypted form. Thanks to MFT, Trojans that are often smuggled into file attachments no longer stand a chance, as the attachments are scanned.
Use SEEBURGER technologies such as the Invoice Delivery Service, the Invoice Portal Service or the SAP integrated solutions Purchase-to-Pay and smart-e-Invoice-Outbound to eliminate such fraud in advance.
A professional Managed File Transfer solution for the dispatch of personal data, as well as an e-invoicing solution for your electronic invoice exchange provide security, transparency and traceability when transferring your sensitive digital documents.
Thank you for your message
We appreciate your interest in SEEBURGER
Get in contact with us:
Please enter details about your project in the message section so we can direct your inquiry to the right consultant.
Written by: Peter Fels
Peter Fels is Product Manager D-A-CH (Germany, Austria, Swiss) at SEEBURGER for the automated processing of incoming invoices for all non-SAP systems. Mr. Fels has many years of experience regarding the conversion from paper to the electronic invoicing processes.





