Three Steps to Greater Data Security by Improving Your TLS Encryption
The worlds of digital security and data transmission do not stand still, which is why it’s important to keep evolving your encryption protocols. Our SEEBURGER Cloud Services, which process a wealth of sensitive information, are continually updated to ensure they meet the highest security standards.
In this article, we’ll be taking a look at the reasons why we are discontinuing support for TLS 1.1 and reducing the scope of TLS 1.2. However, let’s start by taking a step back with a primer on the basics of TLS.
What is TLS?
Imagine you send a letter to a friend, but you want to make sure that no one else can read the contents. Therefore, you put the letter in a “magic envelope” that automatically seals and can only be opened by your friend. This is a bit like what TLS does when you are on the internet. TLS is short for Transport Layer Security, a cryptographic protocol that enables secure communication over a computer network.
TLS is widely used on the Internet:
| Websites | Data transmission | Voice over IP | Chat | |
 |
 |
 |
 |
 |
| Websites that you visit over HTTPS are encrypted with TLS | FTPS (FTP and TLS) is when the data transfer protocol is secured by TLS. | Extending the session initiation protocol (SIP) with TLS to create SIPS thwarts any attempt to eavesdrop on a conversation. | SMTPS (SMTP using TLS) ensures emails are securely transmitted. | Chat data is transmitted in encrypted form using IRCS (IRC via TLS). |
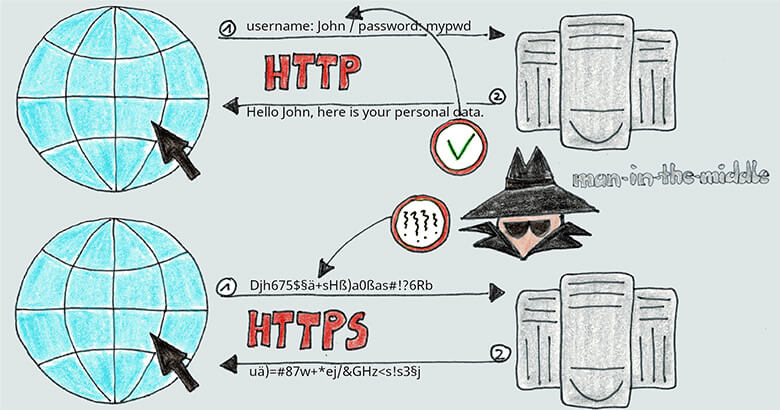
If communication is unencrypted, the data being transmitted is also unprotected and potentially accessible to anyone. Let’s look at a concrete example from electronic data (EDI):
Company X uses AS2 to exchange orders and invoices with business partners. If left unencrypted, this EDI data, which contains business-critical information such as product quantities, prices and delivery dates, could be intercepted by an attacker (man in the middle attack). This could potentially lead to competitive disadvantages, price manipulation or other business-damaging activities. However, if you use TLS, all data traffic is encrypted. Even if an attacker can access a data stream, it’s extremely difficult to read the transmitted information. Although some customers may be concerned that it’s challenging to implement, the benefits of TLS far outweigh the potential risks by creating a secure and trusted communications infrastructure.
Without TLS |
With TLS |
|
|
Risk of interception Without TLS, data is not encrypted. This means that it is transmitted over the network in plain text, which is particularly problematic when it comes to sensitive or confidential information. |
 |
Data protection
TLS encrypts the data that is sent back and forth between two systems. Even if this data were intercepted, nothing could be done with it without the correct decryption key. |
| Identity theft
Without TLS, you run the risk of “man-in-the-middle” attacks, in which an attacker uses stolen personal information to impersonate that person in order to cause damage. |
 |
Authentication
TLS ensures that communication takes place between the two intended systems and not with a system pretending to be the communication partner. This prevents “man-in-the-middle” attacks. |
| Manipulation
Without TLS, attackers can manipulate data in transit. This means that someone can change information en route, which can lead to errors, falsified data or even malicious activity. |
 |
Integrity
TLS detects any modification made to the data during transmission by checking the message authentication code (MAC). A MAC is generated by a function that uses both the content of the message and a secret key. This code is transmitted together with the message. |
| Non-compliance with safety standards
Many security standards and regulations, such as the General Data Protection Regulation (GDPR) in the European Union, stipulate that sensitive data must be encrypted during transmission. |
 |
Norms and compliance
TLS ensures that you fulfill legal requirements by complying with safety standards and regulations. |
Not employing TLS could lead to significant security risks and lead to critical problems. These include data loss, unauthorized access and identity theft.
We can see that TLS is important. Employing TLS contributes to making the internet a secure place by ensuring the confidentiality, authenticity and integrity of the transmitted data. It plays a key role in protecting and securing our privacy in this digital age.
What are cipher suites and why does TLS need them?
Think of a secret safe. Your message is the valuable treasure kept in this safe. The cipher is the lock on the safe. Unless you have the right key (the decryption tool) you will not be able to open the safe and access the treasure (the message).
Essentially, a cipher is a code or method of encrypting and decrypting information.

Just as there are different types of lock for a safe, there are also different types of cipher. Some are easier to understand while other are more complex to better protect data.
TLS uses something called cipher suites to determine how data is encrypted and decrypted between two systems. A cipher suite is used during communication and consists of the following components:
| Encryption algorithm | An encryption algorithm is essentially a formula that converts text into an incomprehensible string of characters. Only those who know the right “decryption formula” can restore the original text. |
| Authentication mechanism | Authentication mechanisms are basically methods to confirm identity, such as the correct combination of user name and password, fingerprint scanners, facial recognition, one-time passwords (OTP) or smart cards. |
| Security parameters | Security parameters are defined rules and limits that ensure the security of something or someone. Examples include prescribed password length and complexity, access times, encryption algorithms and access authorizations. |
Choosing the right cipher suite to give you the right level of security in a particular use case is an important decision.
Step 1: Bye bye, weak ciphers!
To stick with our analogy: To ensure that we are only using the strongest locks, we will be disabling the weak ciphers in TLS 1.2. This is like deciding to use only the strongest locks for your secret safe. No more rusty old padlocks!

In order to determine whether a TLS 1.2 cipher is secure or not, there are certain criteria we need to consider. Below are some of the factors which affect the quality of a TLS 1.2 cipher.
| Key length | A secure cipher in TLS 1.2 needs to be long enough. The longer the key, the more difficult it is for would-be attackers to decrypt the key. |
| Authentication | A good cipher should provide authentication mechanisms so that both server and client confirm to each other that they are who they say they are. This prevents so-called “man-in-the-middle” attacks. |
| Perfect Forward Secrecy (PFS) | PFS ensures that even if a server’s private key is compromised, past communications remain secure. Even if an attacker obtains the current private key, they will not be able to decrypt the previous communication as a unique key has been used for each session. Therefore, TLS 1.2 ciphers that support PFS are preferable as they provide an additional layer of protection against potential compromise. |
| Resistance to known attacks | A secure cipher should be resistant to known attacks, such as BEAST or POODLE attacks. Modern ciphers are designed to protect against such vulnerabilities. |
| Encryption algorithms used | TLS 1.2 supports various encryption algorithms. The cipher should use current algorithms such as AES (Advanced Encryption Standard) or ChaCha20 and avoid outdated algorithms such as RC4 or outdated ciphers such as Cipher Block Chaining (CBC). |
| Expert security recommendations and standards | It is advisable to follow proven security standards and the recommendations of security experts. The German Federal Office for Information Security (BSI) or the National Institute of Standards and Technology (NIST) provide recommendations for secure ciphers. |
When configuring TLS 1.2, it’s important to consider the criteria above and ensure that the ciphers used meet current security standards. Experience has shown that it’s worthwhile supporting and having available several secure ciphers. This flexibility means that if a vulnerability is discovered in a particular cipher, it’s not difficult to switch to a secure alternative.
Step 2: SSLHonorCipherOrder – Who decides?
Now that we understand why only strong locks will do, we want to make sure that we are all using them. This is where something called “SSLHonorCipherOrder” comes into play.
SSLHonorCipherOrder is used in the configuration of our SEEBURGER Application Load Balancer (ALB) to control the order of the TLS cipher suites.
Our SEEBURGER Cloud Services use the ALB to control incoming data traffic, distribute loads evenly and ensure optimum performance, scalability and reliability. It analyzes incoming data traffic and forwards requests to the appropriate servers based on predefined rules.

SSLHonorCipherOrder is a setting that instructs our ALB to use the encryption algorithms in a specific order to ensure that the data is transmitted as securely as possible.
When SSLHonorCipherOrder is active, the ALB prioritizes the cipher suites according to a preference list. This setting ensures that we only use preferred secure and robust encryption algorithms.

However, this doesn’t necessarily mean that communication can’t take place if a less secure cipher is selected. Therefore, it’s important to fully analyze the ciphers being used and to gradually deactivate older and insecure cipher suites. This leads to a continual improvement of the security measures by recognizing and removing potential weak spots.
Step 3: Optimizing TLS encryption: Identify, inform and improve!
What’s going to happen to the systems that are still using rusty old padlocks?
We want all the systems to be secure. Therefore, we’re reaching out to our customers who are still using old padlocks and asking them to update to a shiny new lock with optimum TLS encryption.
Let’s work together to make our SEEBURGER Cloud Services even more secure for you. We are successively activating the SSLHonorCipherOrder parameter on our application load balancers to ensure that all of us are using the most secure ciphers.
Should we identify that you are using vulnerable cipher suites, we will be reaching out to you and encouraging you to switch to the latest security standards. Let’s work together to make sure that SEEBURGER Cloud Services stay highly secure.
Would you like to know more about which ciphers we’d recommend for you? We’d love to hear from you!
Thank you for your message
We appreciate your interest in SEEBURGER
Get in contact with us:
Please enter details about your project in the message section so we can direct your inquiry to the right consultant.
Written by: Ramona Becker
Ramona Becker has worked as a project and product manager at SEEBURGER since 2008. She spends her time working out the technical and organisational considerations of integrating innovative ideas into our product portfolio. In her spare time, her family benefits from her organisational skills. She is also an avid DIYer and loves being creative.